The plans you refer to will soon be back in our hands. A tremor in the Force. The last time I felt it was in the presence of my old master. Don’t act so surprised, Your Highness. You weren’t on any mercy mission this time. Several transmissions were beamed to this ship by Rebel spies. I want to know what happened to the plans they sent you. You mean it controls your actions?
Muhammad Awais
Let’s take a brief look at the FreeRTOS operating system, and the FreeRTOS+Nabto platform. It’s the market-leading, real-time operating system (RTOS) for embedded systems that is not only open-source, high quality and well supported – but also provides strong cross-platform support across 33 different architectures, access to high-quality training and information, pre-configured example projects and a growing user community.
Furthermore FreeRTOS is available in a high-reliability TUV-approved version for demanding, safety-critical applications – providing peace of mind to commercial users, with strict configuration management to ensure high quality development of the FreeRTOS project’s code, and FreeRTOS is free to embed in commercial products without any requirement to expose your proprietary source code.
By combining the FreeRTOS real-time operating system with the patented Nabto peer-to-peer remote access communication platform for embedded systems, you can harness a simple and secure HTML5 or native application interface for your end users, along with an adaptive and flexible data-acquisition interface for data collection, central analysis and monitoring systems.
The resulting combined system brings simplicity, platform independence, inclusive cloud hosting services and entry level access to Nabto’s Internet-of-Things solution together into an interesting easy yet powerful real-time platform for use with embedded Internet-of-Things systems.
FreeRTOS+Nabto is a small piece of C code that, when integrated into an embedded networked device, allows that device to be remotely accessed and controlled through a rich web-based or native iOS or Android app-based interface or intelligent data acquisition system – consuming less than 23 Kb of flash in a typical system including both the FreeRTOS kernel and the IP stack.
Each device has a unique URL, allowing the device to be automatically located across the Internet, and the Nabto technology allows secure, authenticated and bandwidth-efficient peer-to-peer connections to be established even when the device is deployed behind a NAT firewall which removes the complexity of configuring firewall penetration for embedded Internet-of-Things devices in enterprise environments.
FreeRTOS+Nabto enabled devices can also be accessed over the local network in the absence of Internet connectivity. As FreeRTOS+Nabto is a new, simple, cross-platform and fully integrated solution for the Internet of Things, it provides a cloud infrastructure that enables IoT devices to be accessed through a rich user interface running in a web browser or a smartphone app – requiring the device itself to only supply the live sensor data and no other components of the interface, supplying this data via UDP in a lightweight way.

This means that the embedded devices themselves can be kept simple, power-efficient and lightweight – the use of cloud technologies means small FreeRTOS+Nabto devices can be given rich user interfaces without the need for any on-board filesystem or a TCP/IP stack, only relatively lightweight UDP/IP networking support.
These rich user interfaces can be accessed locally via the LAN or anywhere in the world via the Internet, from a computer, tablet or smartphone, with local device discovery and unique and resolvable URLs for each FreeRTOS+Nabto device provided over the chosen domain (LAN or Internet), solving the traditionally difficult problem of naming and uniquely identifying devices in large Internet-of-Things networks.
Using FreeRTOS+Nabto you can connect to a remote IoT device wherever that device is at the time of the connection simply by knowing the device’s unique URL, and being securely authenticated as a legitimate user, with the system handling all the networking, routing and encryption necessary to securely network your IoT devices, address and find them – across the LAN or across the Internet.
All you need to do as an application developer is compile the source code, write a single interface function, and make use of the FreeRTOS+Nabto fully managed cloud service. Instructions and tutorials are provided to make this easy for you, with a strong community of users and the availability of professional support for commercial customers.
Different web content can be served to different geographic regions, moving the burden of internationalisation from the embedded device into the cloud, allowing for even smaller code size and simpler more maintainable designs. All the network routing and protocol details are encapsulated within the FreeRTOS+Nabto product and its inclusive cloud hosting service, enabling FreeRTOS+Nabto to interface with the user’s application source code through a single C function, and enabling FreeRTOS+Nabto to be accessible to users and developers without an advanced level of existing networking expertise.
The FreeRTOS+Nabto platform includes a fully documented live online example that is running on a small real-world microcontroller and a separate project that uses the FreeRTOS Windows simulator. The Windows simulator version creates live virtual FreeRTOS+Nabto nodes on a local network to allow FreeRTOS+Nabto to be evaluated quickly and easily and without the need to purchase any specific hardware.
Although the simulator differs from FreeRTOS running on real hardware in that it does not exhibit real-time behaviour, the ability to set up a development environment, create and experiment with FreeRTOS+Nabto Internet-of-Things applications on a local network before purchasing any specific hardware is still a very useful and attractive capability.
Thanks to the open nature of FreeRTOS, it can be used in a wide range of embedded hardware and become part of your new or existing IoT products. As experts not only embedded hardware but also full idea-to-delivery of products, our consultants and engineers can work with you to meet your goals.
The first step is to join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.
RIOT is a relatively new operating system specifically aimed at applications in lightweight embedded systems, wireless sensor networks and Internet-of-Things applications. Billed as “the friendly operating system for the Internet of Things”, RIOT is competing with similar offerings such as TinyOS, Contiki and embedded Linux.
This may sound complex, however RIOT is aimed at developer friendliness, allowing you to program like you are used to – using standard programming languages such as C or C++, with standard compilers and tools such as gcc, gdb and valgrind, without the developer wasting time having to learn new or complex development environments.
As a real-time operating system that supports C and C++ development, multithreading and a high degree of modularity, RIOT offers all this with a very small, lightweight footprint that is well suited to use with small microcontrollers with limited memory and resources available.
Thus RIOT is aimed at minimising the learning curve needed for embedded programming whilst also being convenient and accessible to developers with established non-embedded programming experience.
The origins of RIOT can be traced back to 2008, when it was originally forked from the output of a German research program called FeuerWhere, that was dedicated to monitoring the location, safety and environmental conditions of Berlin firefighters working in emergency situations.
After being rebranded and expanded, RIOT was released to the public as an open-source project. RIOT is aimed at bridging the gap between fully-fledged Linux operating systems and existing solutions like Contiki and TinyOS that are aimed primarily at wireless sensor networks. The key design goals of RIOT are memory efficiency, energy efficiency in battery-powered devices, modularity and a developer-friendly programming interface.
RIOT is free, open-source software released under a LGPL license, meaning you can freely re-distribute and modify the software. RIOT is a publicly available community project, with an active community of users and developers online where you can learn more about RIOT, get help with writing an application for RIOT from other users and developers, and participate yourself and contribute to open-source kernel development or the integration of support for new platforms, microcontrollers and peripheral devices.
Implementing systems with RIOT isn’t difficult, due to the numerous supported embedded platforms, including the NXP LPC1768, the Texas Instruments MSP430, ST Microelectronics’ STM32 32-bit ARM family and other Cortex-M3 and Cortex-M4 devices, as well as common x86 PCs and x86 embedded systems.
The hardware dependent code is reduced to a minimum and abstracted from the kernel itself. For users that are more familiar with non-embedded programming and software development, you can start with the native port of RIOT, allowing you to run RIOT inside a process on Linux or OSX.
This eases the development and debugging of both RIOT itself and the projects you are developing that run on top of RIOT, allowing you to analyse, develop, test and debug your software with familiar, open tools and platforms such as gdb and valgrind, and to create virtual testbeds of multiple instances of RIOT running on a virtualised embedded hardware platform, running simultaneously and networked together with a configurable network topology, using only your PC.
After development and testing of your code on the native port and using this virtualisation capability, it can easily be deployed to your real embedded devices. Integrated system-on-chip devices containing integrated microcontrollers and radio transceivers on a single chip, such as TI’s CC430F6137, can be used, along with development boards and platforms such as the mBed, ScatterWeb MSB-A2, ScatterWeb MSB-430H, Memsic Telos-B, Texas Instruments’ eZ430-RF2500 and EZ430-Chronos.
You can write your code once, and easily compile and deploy the same code for both 16-bit platforms such as the MSP430 and 32-bit platforms such as ARM.
RIOT is specifically designed with features that are aimed at lightweight embedded devices for wireless sensor networks and Internet-of-Things applications, including very efficient memory and resource use, reliability and robustness in embedded applications running for long periods out in the field without maintenance, a real-time kernel with very low interrupt latency, priority-based scheduling and a tickless scheduler, high energy efficiency, strong code-footprint flexibility and multi-threading with very low threading overhead – making RIOT well suited to the smaller things in the Internet of Things.
RIOT includes core support for IPv6 6LoWPAN (RFC6282 and RFC6775 compliant), UDP, TCP including 6LoWPAN header compression, RFC6550/RFC6719-compliant RPL, and CCN-lite for content-centric networking support.
Furthermore the system includes high-resolution and long-term timers, which is important for embedded applications where timers may need to be running constantly in a device that is deployed for months or years without being rebooted. Other useful tools and utilities are built in, such as support for SHA-256 and Bloom filtering. RIOT includes wiselib built-in, which is a generic C++ algorithm library for heterogeneous, distributed, embedded systems, including algorithms for routing, clustering, time sync, localisation, security, and other common functions.

RIOT includes many built-in drivers for hardware peripherals that allow you to get started with useful hardware applications right out of the box. Some of the supported hardware peripherals include the CC2420, CC1100 and AT86RF231 radio transceivers, the Sensirion SHT11 humidity and temperature sensor, the LTC4150 battery charge/discharge counter, and many other sensors including accelerometers and ultrasonic rangefinders.
Thus with your product needs identified, RIOT can work with a wide range of hardware and base MCUs to form a complete product without “re-inventing the wheel”. If this is of interest, or you need guidance for any or all stages of product design – the first step is to discuss your needs with our team of experienced engineers that can help you in all steps of product design, from the idea to the finished product.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.
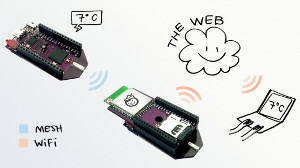
The Pinoccio platform is based around the Pinoccio “Scout” board – a small, inexpensive microcontroller development board based on the Atmel ATmega256RFR2 microcontroller with built-in 802.15.4 2.4 GHz radio, aimed at quick and easy development of wireless, mesh-networked systems and projects without worrying about common challenges such as efficient battery power management, FCC certification and mesh networking protocols.
This hardware offers an integrated Web platform and API so you can easily get started talking to the Web with your project right out of the box, and a built-in lithium polymer battery on every board that is recharged via the same micro-USB port used for programming, with a battery runtime from days up to over a year depending on the software configuration and how the microcontroller and radio are used.
Pinoccio aims to provide an inexpensive but powerful, FCC-certified, power-efficient, mesh-networked and Internet-ready platform for easily accessible Arduino-style development, wireless sensor networks and Internet-of-Things experimentation.
A network of Pinoccio nodes are connected together via a lightweight 802.15.4 mesh network, using the 802.15.4 radio incorporated in every board to network with any other board that shares its Personal Area Network (PAN) ID.
At one or more nodes in the network, the Pinoccio node is equipped with a Pinoccio Wi-Fi board, based on the Gainspan GS1011MEPS 802.11 WiFi module, that connects the 802.15.4 mesh network to your wireless LAN. This means that every Pinoccio node is connected to the LAN and to the Internet, but with a substantially cost and substantially lower power consumption than would be needed if every node in the network was equipped with an 802.11 wireless LAN chipset.
The ATmega256RFR2 draws less than 20mA of current with its microcontroller and RF transmitter running during active transmission – about 10% of the current consumption of a typical Wi-Fi device. The ATmega256RFR2 can be put into sleep states with far lower power consumption as well, with “wake-on-radio” capability to wake up the microcontroller when the wireless network indicates.
With a WiFi connection on at least one node, every Pinoccio board in the mesh network is connected to the Internet. Routing between nodes is supported, so if board A and board C are out of reach of each other, but they can both reach a board B, then B will route packets for A and C to reach each other.
Even if one of the Scouts is out of WiFi range, the others will route its data up to the Web. Pinoccio uses a lightweight mesh networking stack by default – not ZigBee, for example, although there is no reason why advanced users can’t deploy a ZigBee stack on the Pinoccio hardware if they wish.
This coordinator-less mesh network stack is a lightweight alternative to coordinator-based network architectures. Several network configurations are possible, including the traditional coordinator/router/end-node, as well as a completely decentralised peer-to-peer mesh network with routing.
All Pinoccio Scout nodes can be programmed wirelessly, over the air, in a way that is fully compatible with the Arduino IDE – each node in the 802.15.4 network simply appears, with the Pinoccio networking software installed, as a virtual Arduino-compatible serial port in the Arduino IDE.
Without WiFi connectivity, however, users do still have the option of programming each board directly from a PC, via the USB port, just like any Arduino-compatible device, and more advanced users can talk to the chip via traditional hardware interfaces like ISP and JTAG.
You can have your Pinoccio boards scattered all over an area on a wireless mesh network, each doing their thing, and when you need to update the code on one, some, or all of them you can just do so wirelessly from your computer.
If you have Pinoccio boards within an installation, which are difficult to get to, you can easily update their software over-the-air, post-installation, offering a level of convenience that is hard to achieve with other microcontroller development platforms.
You can update a range of boards by listing several of them, or send an update to all boards in the network at once, sending out a single update broadcast. A single update could be sent out to 100 Pinoccio boards if they all need to be updated, and they would all receive the broadcast and update themselves.
The real value of the Pinoccio platform doesn’t just come from the Pinoccio Scout boards, but from the entire stack – from the physical hardware to the API and Web service and back. This includes features like over-the-air firmware updates, optimised mesh networking and the ability to easily move data between multiple Pinoccio boards across the mesh network, to the Web and back again.
Along with easy routing, discovery and beaconing, provisioning a new Pinoccio WiFi bridge node to the larger Web, and the use of low-bandwidth-friendly protocols like MQTT, Pinoccio is a platform that provides a high level of openness and interoperability.
Pinoccio is aimed at being very easy to use, power efficient, Arduino compatible, and completely open source, providing a complete end-to-end ecosystem for building the Internet-of-Things, but with open standards and without proprietary lock-in.
The Pinoccio API completes the last mile between your network of Pinoccio hardware and the Web, allowing you to send and receive messages between your board and the API. However, using the Pinoccio API is totally optional – you own your data, and you can run your own web server to talk to your Pinoccio devices if you wish. Every Pinoccio board can have its own REST-based URL, and it can respond to HTTP POST and GET requests, with the 802.15.4 mesh network and the WiFi bridge doing all the routing for you.
Pinoccio aims to support websockets and webhooks, allowing easy connectivity with Web services, and saves and logs all the data pushed to the API from your devices.
Unlike some other options on the market such as Electric Imp, Pinoccio offers a pre-baked end-to-end platform and Web service with a tightly integrated web-hardware experience to allow everybody to easily, quickly get up and running with a network of devices talking to a Web service – without locking you in and forcing you to only use their servers and Web services with their hardware.
The Pinoccio Scout is open-source hardware – you can download the hardware schematics, board layout and bootloaders freely. Pinoccio strives to use open, industry-standard protocols that are standardised by groups such as IETF and OASIS where possible.
Pinoccio currently uses MQTT as the core messaging protocol for the Pinoccio API on top of Atmel’s Lightweight Mesh Protocol and the IEEE 802.15.4 MAC and radio physical layer, and is considering moving towards 6LoWPAN and RPL in future once these standards are more mature and more work is done in this area in the IETF working group.
One vision of future work that the Pinoccio team has is to have each board accessible from the Internet with a unique IP address, using IPv6/6LoWPAN and a WiFi bridge at one node. Shying away from non-standard protocols, Pinoccio supports HTTP and MQTT-S (MQTT for Sensor Networks) out of the box – but, again, without locking you into any particular choices, if you’re willing to put a bit of work in yourself to implement other protocols.
Pinoccio has good security capability available in every part of the network stack, which is attractive for automation networks and Internet-of-Things applications. The ATmega256RFR2 microcontroller has hardware-based AES128 encryption, along with a true hardware random number generator.
It’s simply a matter of defining a shared secret in your code to enable encryption for the entire mesh network. With the support for TLS sockets in the Pinoccio WiFi module, complete encryption is supported from the device to the Web.
Although still in the beta stage, the Pinoccio system holds great promise as an inexpensive and open mesh networking system which could be applied to new or existing IoT-enabled products.
If this is of interest, or you need guidance for any or all stages of product design – the first step is to discuss your needs with our team of experienced engineers that can help you in all steps of product design, from the idea to the finished product.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.
7 April 2014

FOR IMMEDIATE RELEASE
1 of 1
LX Group named the Champion Professional Services
2014 Australian Small Business Champion Awards
LX Group from Eveleigh has been named Champion Professional Services at the Australian Small Business Champion Gala Dinner and Awards Ceremony held on Saturday 5th April 2014 at The Westin Sydney, with over 900 guests in attendance.
The Australian Small Business Champion Awards is the only national recognition program for Australian small businesses.
The program aims to recognise outstanding Australian small businesses and encourage high standards of excellence in small business practice.
“The Australian Small Business Champion Awards is a way to recognise the efforts of small business people whose efforts contribute to the prosperity and vitality of communities across Australia”, said Steve Loe, Managing Director of the awards. “As a small business owner myself, I know the vision and dedication to excellence required to succeed. These traits have been displayed in abundance by all of our 2014 Small Business Champions.”
Luke Dawson, Solutions Architect of LX Group was presented with an award statuette, certificate and gained national recognition as an industry leader.
Small business from across Australia delivered an impressive array of entries, with winners representing a broad range of industries from all states and territories.
The Awards are proudly presented by Precedent Productions, a small business in its own right, and supported by Sponsors – Castaway Financial Forecasting, BizCover, Jcurve Solutions, Australia Women Chamber of Commerce and Industry, and Key Person of Influence.
– ENDS PRESS RELEASE –
For more information and a complete list of company services, visit our web site at https://lx-group.com.au.
Contact:
LX Group, Elwin Cross, Tel: (02) 9209 4133 Email: [email protected]
Constrained Application Protocol, or CoAP, is an application-layer networking protocol aimed primarily at application in networks of small resource-constrained embedded devices, wireless sensor networks and similar Internet-of-Things applications – helping to enable efficient networking and Internet connectivity with low overheads.
This protocol is particularly well suited to low-power wireless sensor networks with lossy networking and embedded control and automation systems, where such systems need to be supervised or controlled remotely via standard Internet networks.
CoAP is designed to easily translate to HTTP for simplified integration with the web, while also meeting specialised requirements such as multicast support, very low overhead, and simplicity. These are valuable, important features for Internet-of-Things and machine-to-machine networks which tend to be deeply embedded and have much less memory and power available than traditional Internet-connected computers and mobile devices, meaning that efficiency and low overheads are important.
Furthermore CoAP enables embedded web services for even the most constrained devices and networks, while integrating with the web architecture and HTTP. Optimised for applications such as smart energy, home and building automation, asset tracking and cellular M2M, CoAP is emerging as an increasingly popular and important, standardised and interoperable technology in the Internet-of-Things sector.
CoAP includes several HTTP-like functionalities, but they have been fundamentally redesigned for operation in resource-constrained Internet-of-Things and embedded networks. Like HTTP, CoAP identifies resources using a universal resource identifier, and allows resources to be manipulated using HTTP-style methods such as GET, PUT, POST, and DELETE.
The protocol’s transaction layer can include four types of messages: confirmable, where acknowledgement is required, non-confirmable, where acknowledgement is not required, acknowledgement for a confirmable message, or reset, which indicates that a confirmable message is received but the information that would provide the context to allow it to be processed is missing.
CoAP makes use of two message types, requests and responses – using a simple binary header format that is not demanding to parse, and it is at this request/response layer where the REST-based communication occurs. This request/response model may be contrasted with other models such as the publish/subscribe model employed by other significant transport protocols in Internet-of-Things technologies, such as MQTT.
The base header may be followed by further options in an optimised Type-Length-Value format. CoAP is bound to UDP by default and optionally to datagram transport layer security or DTLS, meaning that CoAP can run on many common devices that support UDP or a UDP analogue, whilst providing the optional capability for secure CoAP, which mandates the use of DTLS as the underlying security protocol, providing the potential for good security in applications where authentication and security is an important requirement.
The Internet Engineering Task Force’s Constrained RESTful environments (CoRE) Working Group has done the majority of formal standardisation work with CoAP so far, with a set of IETF Requests for Comments soon to be released surrounding CoAP standards. The standardisation of CoAP by the IETF is in its final stages, and the protocol is soon entering into IETF Internet Standards documents that are aimed at standards-building to better enable the Internet of Things.
In order to make the protocol best suited to Internet-of-Things and and machine-to-machine applications, various new functionalities have been added. The CoRE working group has proposed low header overhead and low parsing complexity as key goals of the CoAP standard-building effort, along with support for the discovery of resources provided by known CoAP services, and mechanisms for simple subscription to a resource and resulting push notifications from that resource.
The mapping of CoAP with HTTP is defined, with RESTful protocol design, allowing proxies to be built to provide access to CoAP resources via HTTP in a uniform way without difficulty.
Access to CoAP resources via RESTful HTTP over TCP is particularly attractive for connecting embedded devices in consumer premises to the Internet, given the near universal availability of HTTP stacks for various diverse platforms.
The RESTful HTTP approach has found success in smaller-scale networks, particularly low-power and lossy wireless networks where message latencies are required to be within the order of seconds, for example for home automation and smart energy management networks.
As some examples of significant adoption of CoAP by major commercial players in the emerging Internet-of-Things industry, CoAP has already found success as a key enabling technology for Advanced Metering Infrastructure (AMI) applications for electricity utility companies deployed within Cisco Systems’ Field Area Network ecosystem.
Sensinode’s NanoService solution uses CoAP, together with their semantic web linking, resource directory and EXI technology, to provide end-to-end embedded web services for the Internet of Things.
If CoAP appeals as a protocol for your next IoT-enabled product or design revision – or you’re interested in any or all stages of the process and need a partner to help meet your goals – the first step is to discuss your needs with our team of experienced engineers that can help you in all steps of product design, from the idea to the finished product.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.
XMPP or the Extensible Messaging and Presence Protocol, formerly known as Jabber, is a communications protocol based on XML (Extensible Markup Language), aimed at message-oriented middleware and applications such as near-real-time instant messaging and presence information. XMPP is designed to be extensible, and has been used for publish-subscribe systems, file transfer, and communication in embedded Internet-of-Things networks.
As XMPP is defined as an open standard and uses an open systems approach of development and application – anyone may implement an XMPP service and interoperate with other implementations. And thanks to its open protocol, XMPP implementations can be developed using any software license and many implementations of the XMPP standards exist for clients, servers, components and code libraries – both open-source and proprietary.
XMPP is well supported as an open standard under ongoing development by standards-makers and organisations such as the Internet Engineering Task Force, which formed an XMPP working group in 2002 to formalise the core protocols of XMPP. No royalties are required to implement support of these specifications and their development is not tied to any single vendor.
In addition to these core protocols standardised by the IETF, the XMPP Standards Foundation (formerly the Jabber Software Foundation) is active in developing open XMPP extensions, including a new series of extensions aimed at allowing Internet-of-Things communications of sensors and actuators using XMPP.
Furthermore, the IEEE is working to define a “Standard for a Smart Transducer Interface for Sensors, Actuators and Devices – Extensible Messaging and Presence Protocol (XMPP) Standard for Networked Device Communication” which, with the backing of the IEEE behind it, is likely to be an influential new standard.
Another advantage of XMPP is that it offers good security, since private XMPP servers can be isolated from the public Intranet, for example on a company Intranet, and strong SASL and TLS security is built into the core XMPP specifications.
The XMPP protocol uses a decentralised client-server architecture where clients do not talk directly to one another, but there is no central server either. By design there is no central authoritative server, but anyone can run their own XMPP server on their own domain or intranet.
Because XMPP uses the XML text format, interfacing machine-to-machine Internet-of-Things networks to machine-to-person communications, where needed, comes naturally.
XMPP features such as federation across domains, publish-subscribe communications, strong authentication and security and XMPP’s name-domain addressing scheme, which helps to navigate the huge breadth of the Internet to get the data where it is needed, are being used to develop XMPP as a powerful tool for implementing the Internet of Things.
XMPP’s easy addressing of a device is especially useful if the data going to or from a device is going between distant, mostly unrelated points, just as in the traditional person-to-person case of XMPP-based instant-messaging communication.
Most XMPP implementations use polling, or checking for updates only on demand. A protocol called BOSH (Bidirectional streams over Synchronous HTTP) lets servers push messages. However, XMPP is not designed to be extremely fast, and XMPP’s idea of near-“real time” communication is close to “real time” on human scales, on the order of a second.
Whilst consideration of timing is important in the choice of Internet-of-Things protocols, this sort of timing is suitable for most applications and is comparable to the timing overheads generally seen in practical systems with other choices of messaging protocols such as MQTT.
Some of the open XMPP specifications under development are specifically aimed at enhancing XMPP standards for Internet-of-Things applications, for example describing how to manage and get information from concentrators of devices over XMPP networks.
Concentrators are devices in sensor networks concentrating the management of a subset of devices to one point. They can be small, such as Programmable Logic Controllers managing a small set of sensors and actuators, medium-sized, for example mid-level concentrators, controlling branches of the network which may use different communication protocols, or entire large systems.
Because XMPP assumes a persistent TCP connection and lacks an efficient binary encoding, it has traditionally not been practical for use over lossy, low-power wireless networks associated with Internet-of-Things technologies. However, recent work in the development of XMPP standards aims to make XMPP better suited for the Internet of Things.
Even though many of the existing and emerging XMPP specifications relating to sensor networks are generally written and can be used by other implementations not based on sensor networks, many of the requirements used to define these specifications come from the requirements of sensor networks and Internet-of-Things applications and infrastructure. These specifications provide a common framework for sensor data interchange over XMPP networks.
One new XMPP specification aimed towards Internet-of-Things applications defines a general concentrator profile that can handle all different types of concentrators available in sensor network architectures, working with multiple data sources.
The XMPP Publish-Subscribe model, comparable to the publish-subscribe model of other protocols such as MQTT of interest in Internet-of-Things applications, describes a system where a tree structure of nodes is published and users can browse this tree structure, publish items on these nodes, and syndicate this information.
XMPP, and the standards and extensions built around it, can enable efficient publication of data collected from large sensor networks, federation of disparate platforms, service discovery and invocation, interoperability of machine-to-machine communications with machine-to-person and person-to-person communications and other advantages in addressing, security and scalability that make it a very promising technology for Internet-of-Things applications. Its strengths in addressing, security, and scalability make it ideal for consumer-oriented IoT applications.
If XMPP appeals as a protocol for your next IoT-enabled product or design revision – or you’re interested in any or all stages of the process and need a partner to help meet your goals – the first step is to discuss your needs with our team of experienced engineers that can help you in all steps of product design, from the idea to the finished product.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.xmpp, internet, of, things, protocol, iot, messaging,xml, lx, group, embedded hardware
Since the early days of computer and networking development in the late 20th century, the open-source hardware and software movement have become a growing force in the world of agile product development.
Using such open-source methods may seem to be a great idea, however there are some potential advantages and disadvantages of choosing to use open-source software and hardware – both using other people’s existing open software or hardware technology, or releasing your own intellectual property as open-source software or hardware for use in the development of Internet-of-Things solutions. What are some of the potential benefits and challenges associated with open source?
For some proponents of open source technology, the most important advantage of open source technology is that it is “free as in free speech”, and this means that software, updates, or other technology or support cannot be withheld by some company – åjust because it decides that you shouldn’t be using their software any more for whatever reason; they can’t just take their ball and go home.
With open-source software or hardware nobody can stop you from using it down the line, and there is at least some form of future access to the technology, even if it is obsolete, less popular or less well supported in the future.
Another key selling point often associated with open software or open hardware is that it is often, if not usually, free as in zero money. Sometimes developers or software vendors may provide an upgraded product, special features or special paid maintenance or support for an open source product – where these special features are commercialised on top of an underlying open-source platform, but generally the underlying open software or hardware technology is freely available for you to work with.
With modern Internet bandwidth, free software can easily be distributed in minutes via Internet download, without the cost of distributing or producing physical disk media. This makes it possible to get free software into the hands of users cheaply and conveniently, which is obviously good for the user, but also good for the software developer because new software can reach many users much faster, getting used in people’s hands sooner and with much greater potential uptake. This can be particularly attractive to small, independent developers.
Obviously in the case of Open Hardware this is a little different, since hardware still costs money to manufacture. However, Open Hardware generally means that design information such as schematics or CAD/CAM design files are freely downloadable for users to look at or potentially incorporate into modified versions or their own electronic designs.
This re-use of existing designs and technology, if you’re happy with the terms of the open-source licenses that may be used, can make design and prototyping faster, potentially getting your product to market (or a potential product or prototype ready for the investment or crowdfunding stage) that much faster.
In many cases, an open source software or hardware project is developed by one person who is often frequently directly accessible to users for direct advice or support. Many authors will provide helpful, patient support – often with a direct level of technical literacy that you’re often not likely to get from commercial “user support” staff reading from a script.
Even if you can’t talk directly to the developer, many open source software or hardware projects will have some kind of associated mailing list or web forum for community discussion, where other users or developers can help you out with advice and support.
Open source software and hardware allows you to get “under the hood” with the design details in a way that you can’t with proprietary technology. This means that you can inspect the engineering, fix problems, identify potential vulnerabilities, and extend or modify the engineering to suit the needs of your application. This is clearly in contrast to closed software or hardware where you are basically at the mercy of the commercial developers when it comes to future development suggestions, security advisories or bug fixes.
One argument in favour of open source technology is that it can be more secure – with many developers and users looking over the source code, security vulnerabilities become much more visible. Whereas closed source software depends to some extent on “security through obscurity”, open source software brings with it an expectation that having lots of users and developers looking through open-source code, maintaining, developing and tweaking it results in better, more secure software – where potential vulnerabilities are detected and corrected.
Applying this sort of “peer-review” to open source software means that the white-hat hackers are able to keep ahead of the black-hat hackers – or, at least, any unfair potential advantage that the black-hat hackers have is minimised.
Nevertheless, we must recognise that this applies a bit differently to hardware than it does to software. If a security vulnerability is discovered in a piece of software and it is openly discussed, a patch can rapidly be developed to correct it and deployed freely to everybody using that software, quickly and easily, thanks to the Internet.
However, if a security vulnerability is discovered in some hardware system which is used by tens of thousands of customers worldwide, what happens if it is not possible to deploy a software or firmware update to correct the problem?
If fixing the vulnerability requires actually buying new hardware to replace an otherwise mostly functional hardware device it is clear that customers may be reluctant to do this, and many systems may be left insecure. In such a situation, if a security vulnerability is discovered and discussed openly then this can easily have more negative effect on security than it does a positive effect, at least in the short term, or in small businesses or home environments where the hardware upgrade may be financially prohibitive.
Another potential advantage of open source technology is that it encourages commercial technology companies to try harder to make their own offerings more attractive, and it encourages innovation and competition – especially when the agility and speed of development by individual open source software or hardware developers, or small businesses, is taken into account.
Open source technology raises the bar, effectively, by saying to customers that this certain set of functionality is what you can get “free as in free beer” – and, to be honest, this is as far as it needs to go for “open source motivation” with some customers. This sends a message to commercial vendors that they may need to offer superior functionality, superior support or usability in order to remain competitive with open-source offerings.
Commercial developers can’t rest on their laurels, and are constantly motivated to innovate and improve their product. Otherwise, an open source product will come along that eats their lunch – as long as it is providing a comparable level of quality, usability and support.
On the other hand, smaller existing commercial hardware or software offerings may not be able to compete with a product that is available for free, and some may argue that open source competition can create a situation to anticompetitive “dumping” – dumping a whole bunch of product on the market at low or no cost in an effort to drive prices down, potentially forcing competitors out of business.
Thus when considering the use of open-source technologies for your next product design or iteration – there are many perspectives to take into account. Do you keep your product “open” and take advantage of the cost savings – but risk higher levels of competition? Or do you work with a closed or existing commercially-available ecosystem?
There’s much to consider, and if you’re not sure which way to turn – the first step is to discuss your needs with our team of experienced engineers that can help you in all steps of product design, from the idea to the finished product.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.
With more and more embedded computing capability, networking and Internet connectivity inside everyday systems such as household appliances, security systems, home heating and lighting systems and even cars, information security has become a potentially important consideration in devices where it wouldn’t previously be considered important – potential security threats may be lurking in embedded systems in a growing number of everyday devices.
Nowadays it isn’t just familiar personal computers that are connected to the Internet – embedded computers are more ubiquitous and are also increasingly connected, and with that connectivity and computational power comes new security threats hiding in new places.
Internet-of-Things networks, smart home automation and persuasive connectivity and embedded computing bring with them exciting new opportunities – a connected home can allow you to log in to your home network before you leave work in the evening to turn on your central heating and your oven, or allow you to log in to your home security system from your smart phone in response to an alarm notification, check your security cameras and reset your alarm if there isn’t a problem.
Unfortunately, these new opportunities do potentially bring with them a new set of security threats. Whilst most consumers are now aware that their personal computers and smart phones are potentially vulnerable to malicious software or network attack, few are aware of the potential threat to other electronic devices.
The Internet of Things may be in its infancy, but threats already exist. For example, computer worms are known to exist that are designed to target embedded devices such as cable and DSL modems and other low-power embedded devices based on architectures such as ARM and MIPS – platforms that are associated not with personal computers, but with the Internet of Things and embedded devices such as modems, routers, industrial control systems and set-top boxes.
Malware exists that adds infected modems and routers to botnets that can be used to support attacks, such as distributed denial of service attacks, on other networks and systems.
What is particularly worrisome about these kinds of threat is that in many instances, the consumer may have no idea that these types of embedded computers are vulnerable to this kind of malicious attack. Devices such as modems or routers may “hide in plain sight” containing malware, and spread it back to personal computers on the same local network.
Once these PCs have been disinfected – or being “trusted” to remain online all the time, directly connected to the Internet in many cases, without being disconnected or decoupled from the Internet as other computers may be to prevent malicious attack or infection in a security-conscious environment.
Many users may think about hardware upgrades to devices such as network routers rarely, if ever, and they may never bother with firmware upgrades and patches – or even with ever changing passwords and login details for configuration of these devices away from their default settings.
In one prominent incident, Trendnet, an organisation that markets Internet-enabled security cameras and baby monitors, shipped some of their cameras with faulty software that left them open to online viewing, and in some cases listening, by anyone on the Internet who was able to discover a camera’s IP address.
The private camera feeds of hundreds of consumers were made public on the Internet. When this vulnerability became public, people published links to the live feeds of hundreds of the cameras, displaying children sleeping and people going about their daily lives. But these devices were not infected with any malware – they were simply designed and sold with negligible security measures in place, relying only on “security through obscurity” and allowing anyone to simply access them if they knew how.
Within the last few years, we have seen a huge range of new Internet-connected and networked embedded devices emerge, from household thermostats to light bulbs to TVs to cars. Although the Internet of Things is still immature, the number of Internet-enabled devices is beginning to explode. According to Cisco Systems, there are more than 10 billion connected devices on the planet – more devices than there are people – and they predict that the world will reach a population of 50 billion connected devices by 2020.
This huge population of connected devices obviously brings with it an increased potential for security vulnerabilities, and an increased need for security awareness, both by consumers and by device manufacturers. Consumers should be aware that just because an electronic device doesn’t possess a display or a keyboard, that doesn’t mean it is not potentially vulnerable to attack. All devices that are connected to the Internet – via Ethernet or Wi-Fi, and perhaps even indirectly – via Bluetooth or 802.15.4 wireless networks, looking into the future – need to be secured.
Consumers should pay attention to the security settings on any device they purchase, and disable capabilities such as remote access if they aren’t needed. Default passwords should be changed to unique, strong passwords that don’t use common, easily guessable numbers or dictionary words.
Furthermore end users should also regularly check manufacturer’s websites to see if there are any updates to software for their devices, since manufacturers will often patch security vulnerabilities with software updates if they are identified. And since network routers and modems are essentially the gateway between the Internet and other devices on the network, keeping these up-to-date and secure is very important.
However almost all security threats and possible incidents can be neutralised before the product reaches the end user. By designing appropriate levels of security into products – including various fail-safes such as mandatory passwords, firmware updates and better documentation and user education, a safer and more reliable IoT can be possible.
If you have a new product idea or an existing version that needs updating, we can take care of all facets of design and prodiucting – including the right security and user-interface to negate as much risk as possible.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.
The Internet-of-things market is growing exponentially – and to some observers it may seem to be an unchecked industry with regards to standards and compatibility. However it isn’t too late to define workable standards – and just that is being done with the International Telecommunications Union’s Internet-of-Things Global Standards Initiative.
In case you’re not familiar with it, the International Telecommunications Union is a specialised agency of the United Nations that is responsible for issues that concern information and communication technologies.
This group coordinates the shared global use of the radio spectrum, promotes international cooperation in assigning satellite orbits, works to improve telecommunication infrastructure in the developing world, and assists in the development and coordination of worldwide technical standards – ITU’s standards-making efforts are its best known and oldest activity.
The ITU’s Internet of Things Global Standards Initiative (IoT GSI) is an initiative of the ITU’s standardisation group that promotes a unified approach for the development of technical standards and recommendations to enable the best possible standardisation and interoperability of the Internet of Things on a global scale.
This international initiative of standardisation has the potential to benefit everybody, from the developers and vendors of Internet-of-Things products and solutions through to consumers. Recommendations developed by the IoT GSI are developed in collaboration with other standards developing organisations – allowing developers, vendors and providers working in the emerging Internet-of-Things industry worldwide to offer a wide range of Internet-of-Things technologies in a standardised and interoperable way. The IoT-GSI also aims to act as an umbrella for further development of IoT standards worldwide.
The purpose of IoT-GSI is to provide a visible single location for information on and development of IoT standards, these being the detailed standards necessary for IoT deployment and to give service providers the means to offer the wide range of services expected from the IoT with a high degree of global standardisation.
By building on the work of other ITU standardisation group efforts in other areas such as network aspects of identification, ubiquitous sensor networks and machine-to-machine communications – the ITU can hopefully bring together different IoT-related standardisation groups both within the ITU and in the wider industry to develop detailed standards for IoT deployment.
From the global perspective of technical standardisation, the IoT can be viewed as a global infrastructure for the information society, enabling advanced services by interconnecting physical and virtual things based on new, and existing, interoperable information and communication technologies. ITU sees enormous potential in the Internet of Things, and hence enormous value and importance in these standardisation efforts, harmonising different approaches to the architecture of the IoT worldwide.
The ITU sees the IoT GSI as important because the deep changes to the fundamental approaches being taken to the provision of situation-aware telecommunication services from network-connected things, and the associated breadth of topics that need to be addressed, are well beyond what could be covered within any particular study group following routine standards development processes.
Furthermore the GSI also provides essential external visibility for the ITU standardisation group’s work, and is a clear and obvious place to go for information on the sector’s work in this particular area. Indeed, it serves as a banner under which to unify all the IoT-relevant activities being carried out within the ITU standardisation group.
Once finished, the IoT GSI aims to have developed a consistent definition of what the Internet of Things actually is, to provide a common working platform bringing together different standards-making, industry and academic representatives, and to develop consistent standards for IoT deployments – taking into account the work already done in other standards development organisations, and recognising that global coordination is the key to widespread success of the IoT.
To meet these objectives, the ITU Joint Coordination Activity on the Internet of Things (JCA IoT) was formed in 2006, bringing together representatives from numerous standards developing organisations, including industry forums and consortia, working in IoT-related areas.
The Joint Coordination Activity provides a platform to exchange IoT information and discuss coordination matters, avoiding overlap and duplicated effort. One of the activities of the JCA is to maintain the ITU’s IoT Standards Roadmap that includes standards from the worldwide ecosystem of standards development organisations that are either approved already or presently under development.
ITU’s IoT-GSI acts as an umbrella for the various standardisation efforts worldwide. Founded on the principle of international cooperation between governments and the private sector, ITU represents a unique global forum through which governments and industry can work towards consensus on a wide range of issues affecting the future direction of this increasingly important industry.
The technology community has highlighted a need to focus standards work in one place, distributing expert resources efficiently and avoiding the emergence of competitive approaches and the GSI responds to this, promoting a unified approach for the development of technical standards and recommendations in order to best enable the IoT efficiently and consistently on a global scale.
Recommendations developed under the IoT-GSI by the various ITU standardisation groups in collaboration with other standards developing organisations will enable technology and service providers worldwide to offer the wide range of services and products that are expected to emerge from the Internet-of-Things industry in the most interoperable and consistent way.
Although doing so may be tempting from an economical perspective, ignoring standards in your IoT-enabled product design could cost you more in the long term, by losing interoperability with other systems – or even scaring off potential customers. Therefore it’s important to be aware of the options in the market and how they can benefit your situation.
Here at the LX Group we have experience in developing IoT systems using various platforms, and can help with any or all stages of product design – to bring your ideas to life.
To get started, join us for an obligation-free and confidential discussion about your ideas and how we can help bring them to life – click here to contact us, or telephone 1800 810 124.
LX is an award-winning electronics design company based in Sydney, Australia. LX services include full turnkey design, electronics, hardware, software and firmware design. LX specialises in embedded systems and wireless technologies design.
Published by LX Pty Ltd for itself and the LX Group of companies, including LX Design House, LX Solutions and LX Consulting, LX Innovations.